
Halley
Halley is a kernel-powered process tracing tool built with eBPF and Rust. It captures real-time exec events directly from the Linux kernel, displaying each process execution with precise metadata like PID, UID, parent process, and timestamp. Designed for speed, safety, and clarity, Halley runs with minimal overhead and zero data tampering, making it ideal for developers, system engineers, and security researchers who need trustworthy visibility into their Linux system

Minimal permissions and safe execution
Halley requires elevated privileges only to load the eBPF program (typically via sudo or with CAP_BPF and CAP_PERFMON capabilities). It performs no packet capture, no syscall injection, and writes nothing to disk making it safe for production and security-sensitive environments.
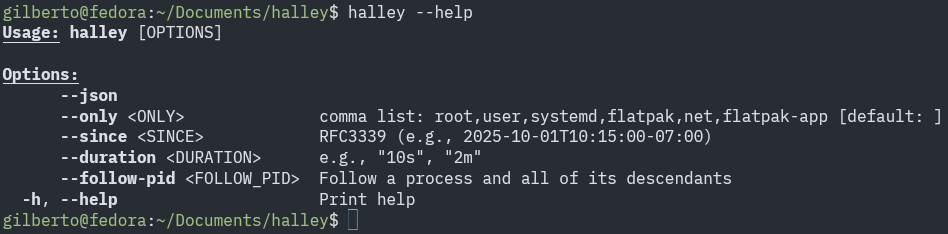
Real-time process tracing
Halley attaches to the sched_process_exec tracepoint in the Linux kernel, allowing it to capture every process execution (execve) event as it happens. It records details such as the timestamp, PID, PPID, UID, and the command name (comm), providing a continuous live stream of process activity.
Rust user-space layer
Halley attaches to the sched_process_exec tracepoint in the Linux kernel, allowing it to capture every process execution (execve) event as it happens. It records details such as the timestamp, PID, PPID, UID, and the command name (comm), providing a continuous live stream of process activity.
Portable CO-RE (Compile Once – Run Everywhere)
Built with eBPF CO-RE support, Halley’s kernel component adapts automatically to different kernel versions using BTF (BPF Type Format) information from vmlinux.h. This ensures reliable compatibility across distributions without recompiling for each kernel.